Main Content
Malware

What is meant by malware?
Malware is a general term for programs used by cybercriminals to deliberately attack computers, smartphones, or entire IT systems. In contrast to phishing or social engineering—which focus on gathering data or exploiting human weaknesses—malware is designed to manipulate or damage technical systems.
Malware is especially dangerous because …
… it often infiltrates systems undetected;
… in the worst case, it can spy on data, disable devices, or block access to important files;
… it can spread rapidly and infect multiple systems at once.
A particularly common type of malware is ransomware. In this case, attackers encrypt your data and demand a ransom—usually in Bitcoin. However, be careful: Even if you pay, the chances of regaining access to your data are low. Although parts of the Emotet network have been taken down, many malicious programs are still circulating. Typical infection routes include:
- Email attachments: Simply opening them can activate malware.
- Compromised websites: Through compromised sites or links in emails and advertisements.
- Security vulnerabilities: Exploited weaknesses in software or operating systems.
- Unsafe downloads: Files from dubious or untrustworthy sources.
Note: Malware often goes unnoticed at first, running in the background or launching attacks with a delay. Regular and secure backups offer the best protection against data loss.
Examples – What this actually looks like:
Attackers also rely on common, everyday communication channels when spreading malware. Most often, they attempt to deliver malware via a manipulated attachment or a malicious link embedded in an email that appears harmless at first glance. These messages often look trustworthy and create a sense of urgency or routine to prompt you to act without thinking.
Below, we present two real-life examples from the past in which members and affiliates of Philipps University were specifically targeted with malware via email.
Inhalt ausklappen Inhalt einklappen Example 1 - Links
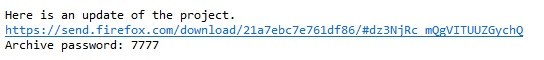 Text of the malicious mail
Text of the malicious mailAttackers often use seemingly trustworthy cloud services like Google Drive, Dropbox, or Firefox Send to distribute malware. As a result, the included links can appear legitimate at first glance and may tempt you to click without thinking. Always carefully verify whether you are actually expecting a download in such messages, and look out for unusual parts or character strings in the link. Be especially cautious with unexpected or unsolicited download links!
Inhalt ausklappen Inhalt einklappen Example 2 - Attachments
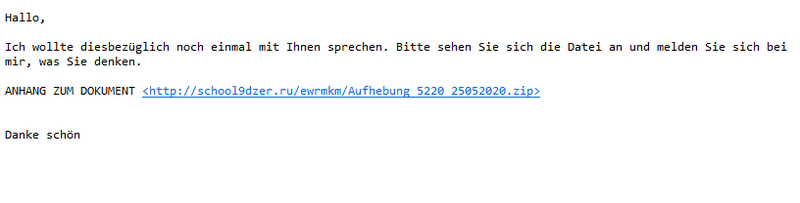 Screenshot of a Qakbot Phishing-Mail
Screenshot of a Qakbot Phishing-MailIn some cases, attackers do not use trusted cloud services and instead send their malware directly as an attachment. Malware is often hidden in seemingly harmless Office documents or archive files such as *.zip or *.rar. Be especially cautious with unexpected email attachments and only open them if you can clearly verify their source and content.
How can you protect yourself?
Warning signals
- Unexpected emails with attachments or links
- Unknown or unusually written sender addresses
- Urgent calls to action (“open immediately,” “act now,” “install this”)
- Office or archive files attached (*.docx, *.zip, *.rar)
- Links to cloud services with long or cryptic addresses
- Grammatical errors or unusual phrasing
Protective measures
- Stay calm and carefully check emails, attachments, and links before reacting.
- Check sender addresses and their requests, and if in doubt, ask for clarification in person or by phone.
- Hover your mouse over links to see the actual destination address.
- Never open unknown or unexpected attachments without verification.
- Keep your operating system and software up to date and install updates promptly.
- Uninstall programs and apps you do not need to reduce potential attack surfaces.
- Regularly make complete and secure backups of your important data so you can react quickly if something happens.
Conclusion: Stay vigilant, review emails and attachments critically, and protect yourself with regular updates and backups.
Download our cheat sheet on recognizing phishing emails
Attend our IT security training to effectively protect yourself against cyberattacks
When the child falls into the well ...
Despite all precautions, malware can still end up on your device—especially in stressful situations or when dealing with particularly convincing emails. It is important to stay calm and act quickly to prevent further damage. Therefore:
1. Step: Immediately disconnect your device from the network (disable Wi-Fi or unplug the network cable) and remove external storage devices such as USB sticks and hard drives to contain the spread.
2. Step: Do not comply with ransom demands, even if your data is locked.
- By paying, you support the attackers and enable further criminal activity.
- There is no guarantee you will actually receive a decryption code.
- For many types of ransomware, decryption tools are already available online.
3. Step: Immediately inform your IT administration or a professional!
Keep calm & report an IT emergency.
Please contact your IT administration and/or:
IT emergency phone number: 06421 28-28281
E-mail: it-sicherheit@uni-marburg.de