Main Content
Social engineering

What is meant by social engineering?
Social engineering is not a new master's degree at a university of applied sciences, but another method used by hackers to get you to do things you don't actually want to do. As with phishing, the attackers are usually after your credit card or account details, your passwords or other sensitive information such as unpublished research results.
These attacks are particularly perfidious because ...
... they exploit human rather than technical loopholes or errors.
... they exploit our willingness to help, our trust or our respect for superiors.
In social engineering (e.g. gift card scams), the target is not your computer or smartphone, but you:
- An attacker typically spies on you first via your social media profiles and uses all available sources to gather as much information about you as possible.
- You then receive a personalised email with an authentic-looking request. For example, a supposed acquaintance could ask you for the latest results of an ongoing experiment for an important study. In all cases, the attackers are behind it.
Be careful! Social engineering is multimedia, i.e. the attacks can be carried out by phone, email, text message or direct message in any app.
Example - How hackers try to manipulate you:
The attackers are broadly positioned. Many of us are familiar with the example of alleged IT support with a foreign accent who urgently needs to solve PC problems on your computer. All you need to do is install remote maintenance software and provide a password. Another example would be fitters who want to check your heating and kindly suggest that you go for a coffee in the meantime. It is particularly helpful for them if you do not lock your computer and they can access your data.
Just as you would not entrust your house keys to strangers without hesitation, you should also be careful with your access to data in the digital world. While your house is protected by a lock, secure passwords and encryption protect your information in the virtual world.
Inhalt ausklappen Inhalt einklappen Straight to the point: A concrete example of social engineering at Philipps University
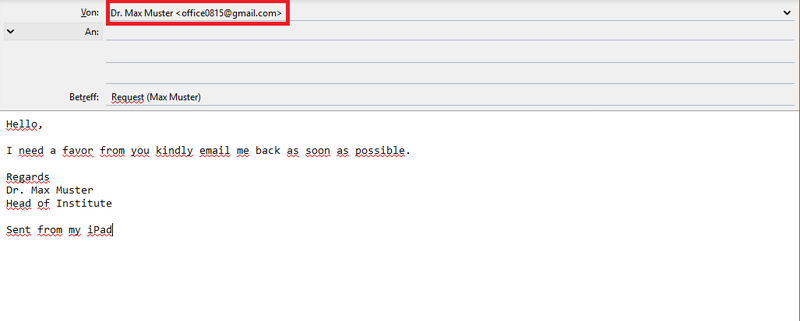 Text of a scam mail
Text of a scam mailIn the past, social engineering attacks at Philipps University were often carried out by email. The screenshot here shows a fictitious example with the real content of such a scam email.
We have highlighted in red how you can recognise that something is wrong with the email. A closer look at the sender's address reveals that the email does not come from Philipps University. This is often the case with scam emails and is reason enough to be cautious. You can find out how to recognise the actual sender of an e-mail on the page on phishing.
Our observation - Note:
In the cases we have observed at Philipps-Universität, the management of an organisational unit often allegedly asks employees to contact them urgently. Once again, it is suggested that everything has to happen very quickly. If you reply to the email, you will be asked, for example, to buy voucher codes, make a transfer to an account that the scammers kindly give you, or hand over sensitive data such as account details or passwords.
How can you protect yourself?
Warning signals
- Unexpected attachments or links
- Unusual requests
- Urgent requests or demands
- Offers that are too good to be true
- Unknown persons
Protective measures
- Stay calm and think before you react.
- For urgent enquiries, always consult your supervisor first.
- Make work-related phone calls in private places, not in public.
- Be cautious when sharing work-related information on social networks.
- Never open unexpected email attachments without checking them first; always ask in person.
- Do not let unknown people into the office unsupervised.
- Always lock your computer (Windows + L) as soon as you leave the workplace.
- Check the sender's address in emails carefully; do not be fooled by the name.
- Never give out passwords to alleged support staff.
Essential: Use secure passwords and encrypt your data.
Download our cheat sheet on recognising phishing emails
Visit our IT security training course to arm yourself effectively against cyber attacks
When the child falls into the well ...
Social engineering attacks can be so sophisticated that you may unintentionally disclose sensitive information or perform unintended actions. It is important not to panic and to address the situation in a systematic manner. Therefore:
Secure evidence and contact the IT administration!
Keep calm & report an IT emergency.
Please contact your IT administration and/or:
IT emergency phone number: 06421 28-28281
E-mail: it-sicherheit@uni-marburg.de