Main Content
Gift card scam

What is meant by gift card scam?
The scam method described here is characterised by the fact that potential victims are persuaded to purchase gift cards and provide the codes to the scammers. The attackers' approach is based on social engineering techniques. In social engineering, it is not the technical device, such as the computer or smartphone, that is the target of the attack, but the person using this device. In addition, scams using gift cards are very popular, and the reasons for this are clear:
- Gift cards are anonymous and can therefore be used by those who know the code
- They are difficult to trace after delivery
- Quick and easy activation of the codes
Due to its high popularity, there are a variety of scenarios in which attackers try to deceive their victims. The following scenarios are the most likely:
- Phishing emails
- Phone calls
- SMS / messenger messages
- Fake competitions on social media or websites
- Supposed support staff
Example - How a scam can work (spear phishing):
One of the most frightening aspects of social engineering methods is the targeted search by attackers for vulnerabilities in the curriculum vitae of their victims. This is done with the help of fake identities that are intended to be perceived as genuine. For example, the attackers identify the victim's superiors and use this information for their own purposes - as in this example.
Inhalt ausklappen Inhalt einklappen 1. Information gathering
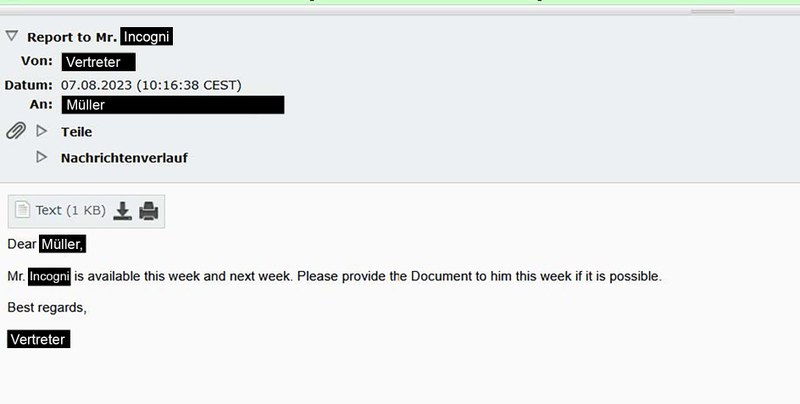
Attackers therefore need information about them at the beginning in order to manipulate them in the best possible way. In this example, an ordinary conversation between a student - Müller (name changed) - and an employee of the university was intercepted. The conversation was about informing the student Müller that the professor is available this week and next week and that he should send the document this week if possible.
Note: An email with time pressure, responsibility and hierarchies is particularly valuable for attackers because they can be exploited in a targeted manner to deceive their victims quickly and easily.
Inhalt ausklappen Inhalt einklappen 2. Attack
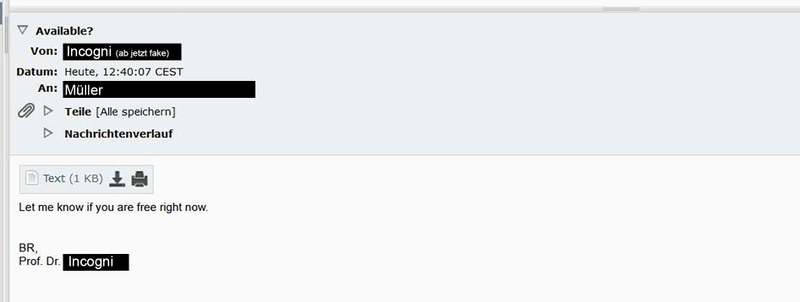
After a very short time, the attacker contacted us under the stolen identity ‘Nauss’ of the professor consulted.
Recognisable anomalies:
- There is no formal greeting.
- The subject line is very short and contains no further information.
- The content is limited.
- The content is aimed directly at you and not at the object of the action.
- The attacker tries to create as much space as possible so as not to overstep any unwanted boundaries and still arouse the other person's interest.What can I do at this point?
To protect yourself in a professional, private or student context, it is advisable to use alternative contact channels such as telephone or face-to-face meetings if you are unsure. It is advisable to check the e-mail address carefully and compare it with the official data. It also makes sense to ask the person for verification.Inhalt ausklappen Inhalt einklappen 3. Exchange
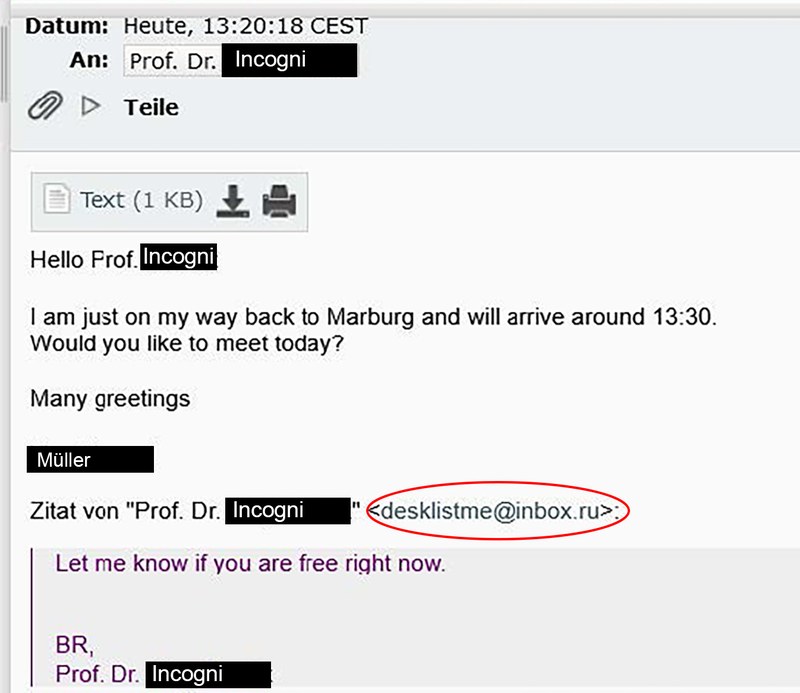
Müller replies to the message from the supposed professor and informs him that he will be back in Marburg from around 1.30 p.m. and asks whether a meeting on the same day would still be possible. The e-mail address ‘desklistme@inbox.ru’, which is assigned to the professor, is more than conspicuous.
Note:
It is important to exercise caution if a person does not respond to a question or does not answer it in the expected way. In such cases, it is advisable to check the situation with due diligence and take further action if necessary. It is also important to check the full email address. Care should be taken with endings such as ‘.ru’, ‘.cn’, ‘.su’, ‘.tk’, ‘.ml’, ‘.ga’, ‘.cf’ or ‘.gq’. The @inbox.ru used here is also a free e-mail address frequently used by hackers. However, it is important to point out that not every ending is automatically categorised as ‘criminal’.Inhalt ausklappen Inhalt einklappen 4. Flattery
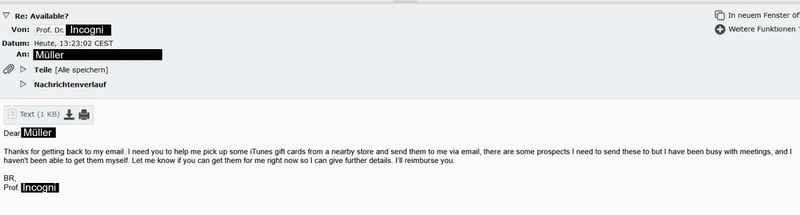
The salutation only appears after a reply has been given. A common approach used by attackers is a polite but intrusive approach to fulfil their wishes, as expressed in the email message ‘Thanks for getting back to my email’, for example. They present themselves as highly involved and rely on the politeness of their counterpart, for example by using the phrase ‘I need your help’. They often exploit power relationships, in this case the attacker pretending to be a professor. In this situation, the person concerned is naturally under pressure. This is because the situation suggests that if they do not fulfil the request, this could have consequences for their studies or work.
Inhalt ausklappen Inhalt einklappen 5. Feedback
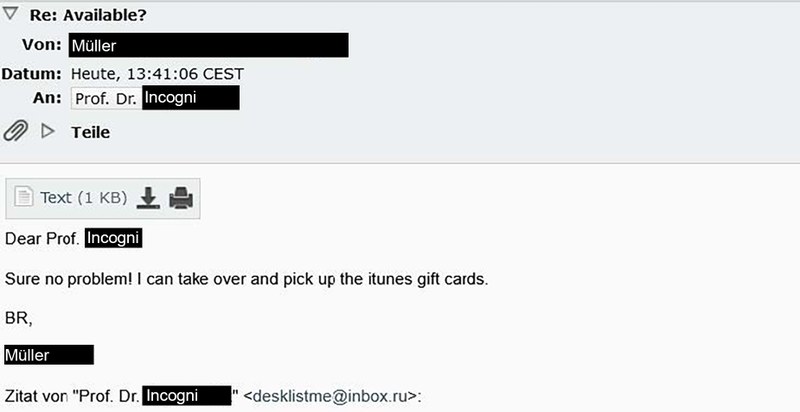
At this point, the scammer's claim has been confirmed by the person concerned.
Inhalt ausklappen Inhalt einklappen 6. Specification
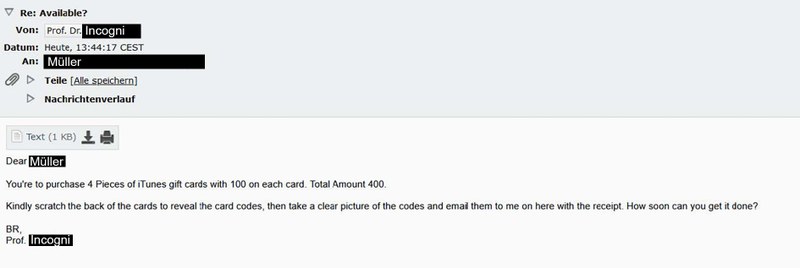
About three minutes later, Mr Müller receives a reply. He is asked to purchase four cards with a total value of €100 each and provide them to "Nauss". To avoid further procurement problems, the scammer naturally states the total value as €400. He also attaches precise instructions explaining to Müller how he should transmit the gift card data. Of course, in such a way that the scammer can get away with it as anonymously as possible. To round off the attack and create even more pressure, the scammer asks directly when the pictures can be sent.
Inhalt ausklappen Inhalt einklappen 7. Pressurisation
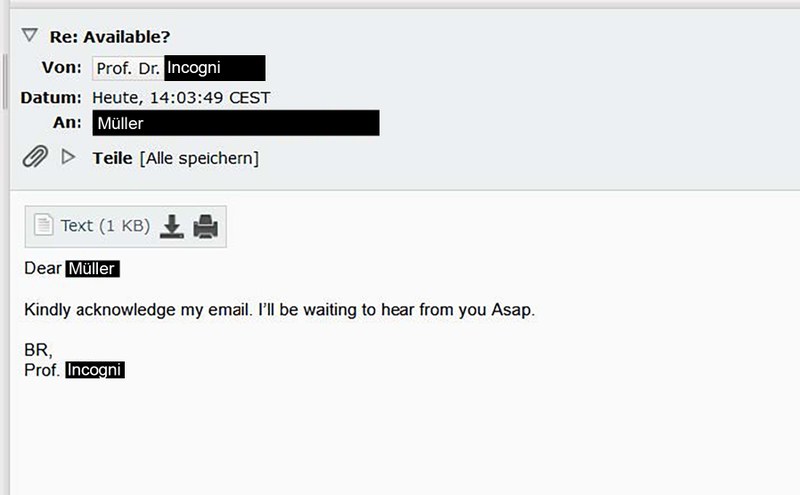
Without a response from Müller, the attacker sends another email within 20 minutes. This serves to build up further pressure. The abbreviation ‘ASAP’ stands for ‘as fast as possible’.
Inhalt ausklappen Inhalt einklappen 8. Success of scam
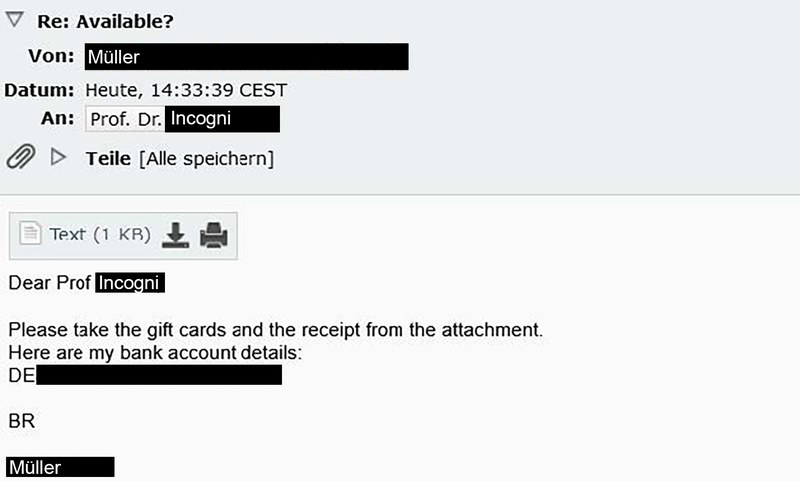
The scammer was then sent the voucher card data and Müller's bank details. The initial theft is complete at this point, but the attackers are usually not satisfied with this. Once a victim has been found, they try to steal as much money as possible.
Inhalt ausklappen Inhalt einklappen 9. Scam trap
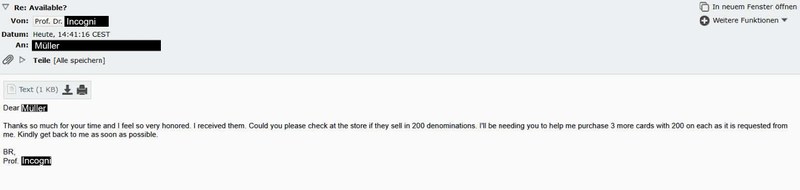
So the next enquiry is made straight away. Now with even higher demands. The amount requested has increased from 400 euros to 600 euros. The approach is still the same: to manipulate you in a polite and slimy manner.
Inhalt ausklappen Inhalt einklappen 10. Repeat
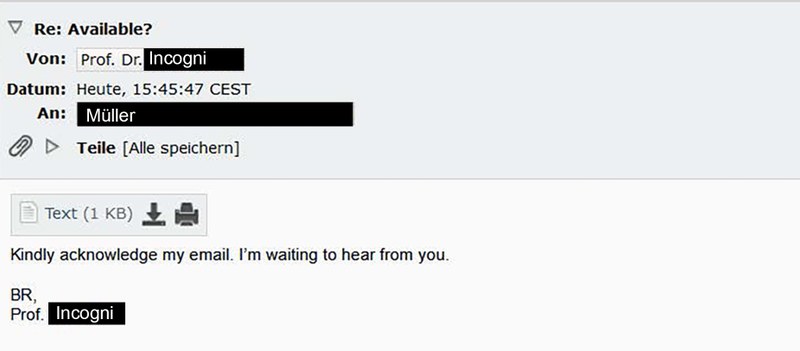
Repeat step 7: Tactics - putting pressure on the person to act.
The exchange then ended.
How can you protect yourself?
Warning signals
- The ending and the name of the email sender address, such as "desklistme@inbox.ru"
- Unsolicited messages or calls requesting quick action
- Request(s) to buy gift cards or provide codes
- If organisations request payment methods that they do not normally offer
Protective measures
- Keep calm and do not react hastily.
- For supposedly urgent e-mail enquiries, always verify the contact person by telephone or other secure means.
- Use private and professional data sparingly.
- Check sender addresses in emails carefully, as these are often forged.
- Take advantage of IT security training courses to familiarise yourself with the latest scams and protective measures.
Please note: When it comes to protection against social engineering (including gift card scams), it is primarily up to you, as you are the target of the attack. You can find further protective measures under: Social engineering
Download our cheat sheet on recognising phishing emails
Visit our IT security training course to arm yourself effectively against cyberattacks
Once the damage is done ...
It can happen that you have passed on gift card codes under stress or through skilful deception. The same applies here: stay calm and act quickly and carefully. Therefore:
Contact the card exhibitor and inform the IT administration!
Keep calm & report an IT emergency.
Please contact your IT administration and/or:
IT emergency number: +49 6421 28-28281
E-mail: it-sicherheit@uni-marburg.de