Main Content
Phishing

What is meant by phishing?
Phishing is a particularly sophisticated method used by cyber criminals to obtain your access data, such as your user name and password. It usually involves gaining access to email accounts, online banking or other sensitive services. In contrast to purely technical attacks, phishing specifically targets the human factor. It exploits our willingness to help, our need for security or our desire to complete important tasks immediately.
Phishing attacks are so effective because ...
... the emails look deceptively genuine (logo, language, names of familiar people/senders),
... they are intended to put them under stress or pressure to act (‘Act immediately, otherwise ...’),
... our trust in seemingly routine enquiries is addressed.
Attention: Phishing is flexible! Such attacks not only reach you by email, but sometimes also by telephone (voice phishing, ‘vishing’), SMS (“smishing”), QR codes (‘quishing’) or even by direct message in social networks.
Examples - Concrete incidents from the university environment:
As a rule, the phishing attack is initially carried out in an inconspicuous manner. You receive an email purporting to be from a trusted organisation, e.g. from supposed IT support, your bank or a well-known online service. This message usually tells you to carry out a specific task with a high degree of urgency. One example is that you are asked to follow a link and ‘verify’ yourself, as your mailbox is supposedly overloaded and you will otherwise not be able to receive any more messages.
Phishing efforts are not limited to e-mails. Phishing links can also be placed on websites themselves - for example in fake adverts, dubious downloads or comment fields. If you click on such links, you often end up on deceptively genuine websites that are only designed to steal your login details or personal information.
Below you can see examples of phishing emails and fake websites that were sent to members and affiliates of Philipps-Universität in the name of IT Support.
Inhalt ausklappen Inhalt einklappen Example 1 - E-mail

To make it easier to identify this e-mail as a phishing e-mail, we have highlighted the relevant parts. The sender's address does not match the official address of the HRZ. The signature contains the name ‘Lorem Ipsum’, which firstly is not a real name and secondly is a dummy text that is not intended to mean anything. Normally, every e-mail begins with a personal greeting. This one, however, does without it completely.
In addition, the text contains grammatically and generally poor formulations, such as:
- ‘Don't ignore to prevent ...’
- ‘Update now to keep your ...’
- ‘To check your mailbox account click here’Please note: If there is no formal address, there is a very high probability that it is a phishing email. If there is a formal address but you are not addressed directly, the probability of an attack remains high.
Inhalt ausklappen Inhalt einklappen Example 2 - E-mail
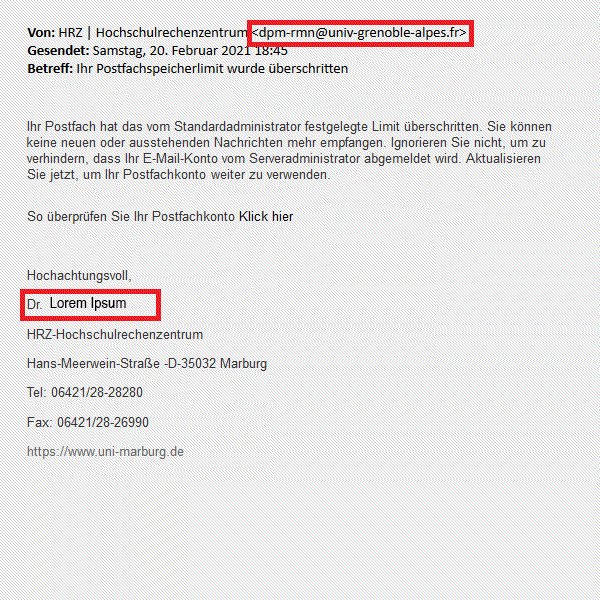
If we look at this email, we immediately notice several conspicuous features: a suspicious sender address, no formal address and a missing signature. But there are other conspicuous features too. The subject line is demanding and completely devoid of content. The phishing link was not placed after the colon, but linked to ‘Click here:’. The link in the emails does not lead to the login page of the university webmailer, but to a fake page of the attackers. The longer you look for anomalies, the more you will find. One example is the double ‘Thank you [...] IT administration ...’ formulation at the end of the email.
Please note: The links behind text passages are opaque and should always be checked. If you enter sensitive data on these linked pages, you run the risk of the attackers being able to access your data.
Inhalt ausklappen Inhalt einklappen Example 3 - Fake Login ILIAS
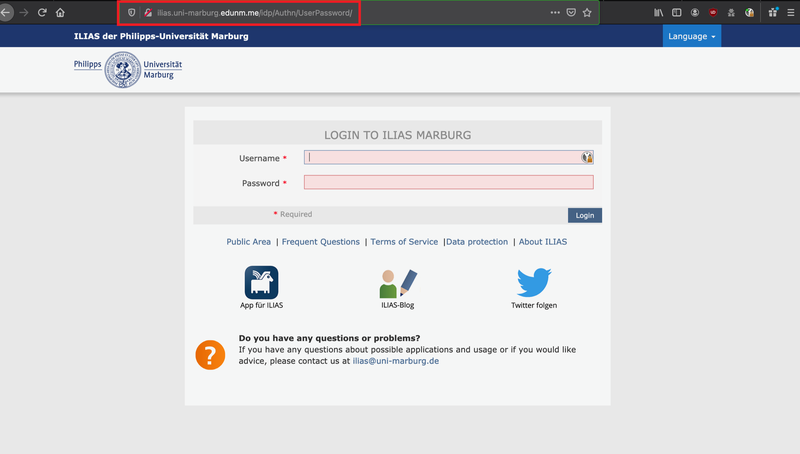
The fake can be recognised by the URL, which we have outlined in red in the address bar of the browser. We would like to point out that this page is not connected to our learning platform. Instead, this link will take you to edunm.me, which is not connected to the University of Marburg. Furthermore, the actual login page is available in German and looks completely different in the original. The aim of this site is purely to steal your data, especially your login data. Therefore: Always check the URL.
Inhalt ausklappen Inhalt einklappen Example 4 - Fake Login Webmailer
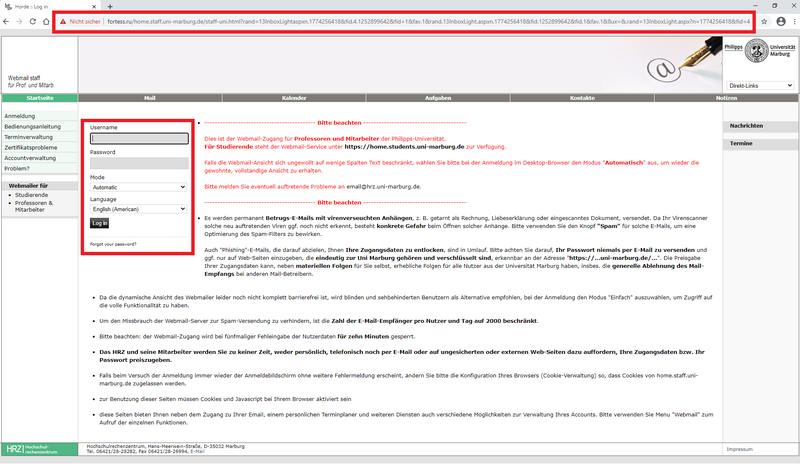
The link leads to the website fortress.ru, which is operated by a Russian organisation and has no connection to Philipps-Universität. In addition, the connection is displayed as insecure. Please note that you always connect to our university webmailer via a secure connection, which is displayed with a green lock in the address bar. Again, the language is set to English by default, but the real university webmailer is set to German.
How can you protect yourself?
Warning signals
- Unusual senders or seemingly familiar senders (e.g. unusual domain endings, transposed letters or foreign-language name components)
- Urgent pressure to act (e.g. "Your account is at risk")
- Unclear or incorrect language
- Incorrect or conspicuous web addresses (see examples)
- Unknown attachments and links
- Payment or action requests
Protective measures
- Stay calm and take your time before responding to emails, even if they appear to be urgent.
- Always check the sender and content critically and, if in doubt, contact the person via a secure, independent channel.
- Check links before clicking on them with your mouse (hover over them) or check them first in a search engine.
- Always open important websites directly via the address bar or saved bookmarks, not via links in emails.
- Be particularly attentive to unusual language, incorrect wording, or strange salutations.
- Never disclose personal or work-related data carelessly; reputable organizations do not ask for it by email.
- Stay informed: Take advantage of IT security training courses to familiarise yourself with the latest methods and protection options.
Inhalt ausklappen Inhalt einklappen Excursus for those interested - What exactly is ‘quishing’?
The term "QR phishing" or "quishing" describes a specific form of phishing in which criminals use fraudulent QR codes to redirect users to fake websites.
- Do not scan QR codes if they come from an unknown or suspicious source
(often found on posted posters, emails or fake forms)
- Generally check the URL carefully after scanning (e.g. for spelling mistakes, different domains)This method is particularly suitable for bypassing e-mail filters - therefore particular vigilance is required!
Inhalt ausklappen Inhalt einklappen Excursus for advanced users - check sender addresses:
Check the sender's e-mail address as follows:
- Outlook: File > Properties > Internet headers
- Thunderbird: More > Show source code (Ctrl + U)
- Uni-Webmailer: More functions > Message source
Look at the lowest Received block that does not contain localhost and compare it with the "From:" field below it. If the e-mail is supposedly from a member of Philipps University, you must not find any external server names in these fields (e.g. mailer.webhostapp000.com).
Download our cheat sheet on recognising phishing emails
Visit our IT security training course to arm yourself effectively against cyberattacks
When the child falls into the well ...
In stressful situations or with well-crafted phishing emails, it can happen that we fall into the net of the attackers. It is then important that we react correctly and quickly to prevent major damage. Therefore:
Change password immediately and inform IT administration!
Keep calm & report an IT emergency.
Please contact your IT administration and/or:
IT emergency phone number: 06421 28-28281
E-mail: it-sicherheit@uni-marburg.de