Main Content
Yubico Authenticator
Instead of generating TOTP codes on your smartphone, as is the case with many other authenticator apps, Yubico Authenticator stores the secret keys securely on a YubiKey hardware token. When you need a code, the app reads the key from the YubiKey, which is plugged into your device or connected via NFC. The advantage of this is that the secret keys never leave the YubiKey. Even if your smartphone is hacked, the keys cannot be stolen.
Key benefits
- Increased security: The secret keys are protected on the hardware token and cannot be accessed via the internet.
- Recoverability: If you lose your smartphone, you can simply install the Authenticator app on a new device and use the YubiKey to recover your accounts. The keys are stored on the YubiKey, not on your smartphone.
- Phishing protection: Since you need the physical YubiKey for authentication, phishing sites cannot simply steal your login credentials.
In summary, the Yubico Authenticator is a security solution that combines the convenience of an app with the hardware security of a YubiKey.
Installation
The Authenticator is available on Opsi-managed PCs in the self-service kiosk. If you administer your own computer, it can be downloaded here. For Linux, the easiest way is to download the AppImage file. The AppImage then only needs to be made executable.
chmod +x yubioath-desktop-<VERSION>-linux.AppImageManaging and using TOTP
In addition to the slots already programmed by the HRZ, the YubiKey 5 offers space for 32 TOTP credentials. Since TOTPs are time-based tokens, the program is necessary for this. The functions of the Yubico Authenticator are to communicate the current time to the YubiKey for the TOTP function and to trigger the YubiKey to recalculate the one-time passwords.
Info: The YubiKey Standard and the YubiKey 4, which we still have in circulation, do not offer this function.
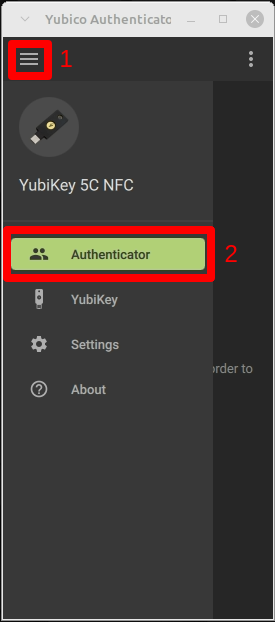
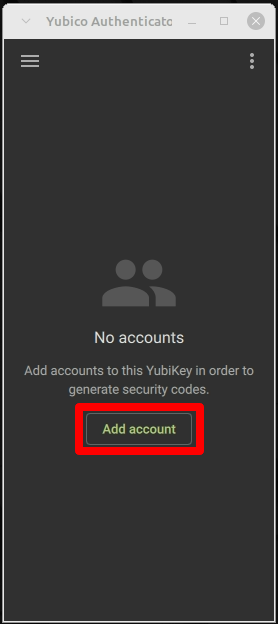
Creating a service is very easy in the Authenticator tool. That is why we recommend this option, especially since the data is stored on the YubiKey and is therefore always available. To do this, click on Authenticator (2) in the menu (1). An “Add Account” window should open here:

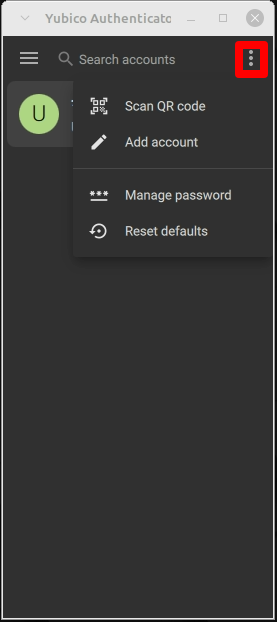
If you have already created a service, you can add more via the menu item at the top right:

The simplest method is “Scan.” Here, a QR code displayed by the application in which you want to set up OATH is scanned from the screen. The Authenticator app can extract all relevant information from this code. Here is an example using the “UMR-HRZ Password Manager” app:


Manual entry also works in this case. To do this, you need the specified security key and the account name. In the main window of the Authenticator, you should now see a column labeled “UMR-HRZ Password Manager.” You can obtain the code by double-clicking on the “UMR-HRZ Password Manager” column. You will then be prompted to press the YubiKey and you will have your code. If the setup is TOTP, this is usually valid for 30 seconds:
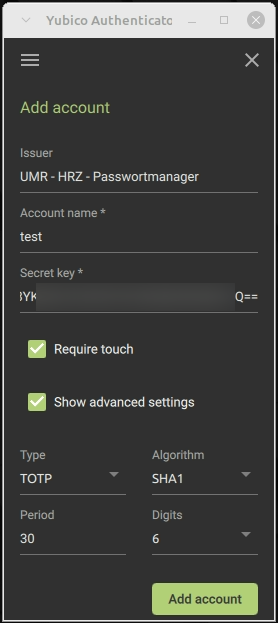

Once you have generated and entered this TOTP code, the service is fully configured. Adding it is always this easy and should go smoothly.